Are you currently looking for a way to improve the security of your organization’s digital assets? Learn about the various benefits of installing a PAM system. You won’t regret it!
Introduction
Pluggable Authentication Modules (PAMs) are a type of security token that can be added to web applications to provide authentication and access control. They allow users to log in using a username and password or another authentication method, such as a biometric identifier.
PAMs can also manage user access levels and track user activity across multiple websites. This is useful for organizations that want to keep track of how users use their resources and identify any potential abuse or unauthorized activity.
These modules are convenient because they allow users to easily switch between different authentication methods without re-entering their passwords each time. This makes them ideal for web applications that accommodate various user profiles.
How to install a PAM system?
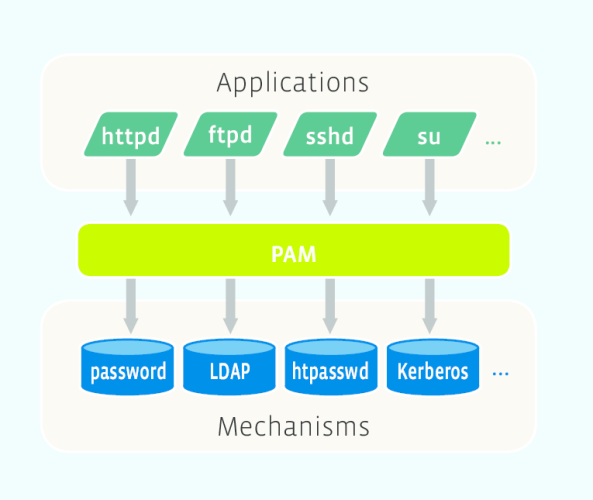
Pluggable Authentication Modules (PAM) are software components that allow users to log in to systems by providing them with unique identifiers and passwords.
To install a PAM system, you first need to identify the types of accounts you want to allow users access to. You can create user profiles for each account type or use system profiles predefined for users of funds. Once identified, you’ll need to make the PAM files for each. These files contain the information required by the PAM system to authenticate users.
To install a PAM system, you’ll need to copy the necessary files onto the server where your users log in. Then, you’ll need to enable authentication for those files by setting up an appropriate security policy. Finally, you’ll need to configure your users’ computers so that they can access those files and use the PAM system.
Security considerations when deploying PAM
You need to deploy a security solution like Pluggable Authentication Modules (PAM) to protect your data and applications from unauthorized access.
PAMs are authentication modules that can be integrated into various applications and systems. They provide users with a flexible and easy way to authorize access to their data using one or more passwords or other authentication credentials.
The advantage of using PAMs is that they can be easily configured and administered to meet your organization’s specific needs. Furthermore, they can be deployed as part of an overall security solution that includes firewalls, intrusion detection systems (IDS), and other components.
There are a few things to keep in mind when deploying PAMs:
- Make sure the module is compatible with your system and applications.
- Choose the correct type of password for your use case.
- Store the passwords securely so that unauthorized users cannot access them.
Overall, Pluggable Authentication Modules are an effective way for organizations to secure their networks against unauthorized access and malicious behavior. Ensure you consider all the relevant security implications when deploying this technology in your organization – it will help protect your data and assets from harm!
In conclusion, Pluggable Authentication Modules (PAM) is a valuable security feature that can help protect your online data from unauthorized access. PAMs allow you to authenticate users who access your system using specific credentials, such as user IDs and passwords. They also provide an added layer of security by verifying users’ identities before they are allowed to access your system.

